Black hat Python : Python programming for hackers and pentesters
Python is the high-level language of choice for hackers and software security analysts because it makes it easy to write powerful and effective security tools. A follow-up to the perennial best-seller Gray Hat Python (2011), the all-new Black Hat Python explores the darker side of Python’s capabilities — writing network sniffers, manipulating packets, web hacking, infecting virtual machines, creating stealthy trojans, extending the popular web hacking tool Burp Suite, and more. By showing how carefully crafted code can be used to disrupt and disable a system, Black Hat Python will help you test your systems and improve your security posture. Insider techniques and creative challenges show you how to extend the hacks, and are sure to make Black Hat Python irresistible to anyone interested in offensive security
Setting up your Python environment — The network: basics — The network: raw sockets and sniffing — Owning the network with scapy — Web hackery — Extending Burp proxy — GITHUB command and control — Common trojaning tasks on Windows — Fun with Internet Explorer — Windows privilege escalation — Automating offensive forensics
Access-restricted-item true Addeddate 2022-12-21 08:01:07 Autocrop_version 0.0.14_books-20220331-0.2 Bookplateleaf 0010 Boxid IA40799304 Camera Sony Alpha-A6300 (Control) Collection_set printdisabled External-identifier urn:lcp:blackhatpythonpy0000seit:epub:a918e60c-7e32-4f13-9eaf-44e2b12a678b
urn:lcp:blackhatpythonpy0000seit:lcpdf:e42ae09b-5882-47af-ab90-3c46def58240
urn:oclc:record:1357511980 Foldoutcount 0 Identifier blackhatpythonpy0000seit Identifier-ark ark:/13960/s2zrzm3zkx0 Invoice 1652 Isbn 1593275900
9781593275907 Lccn 2014953241 Ocr tesseract 5.2.0-1-gc42a Ocr_detected_lang en Ocr_detected_lang_conf 1.0000 Ocr_detected_script Latin Ocr_detected_script_conf 1.0000 Ocr_module_version 0.0.18 Ocr_parameters -l eng Old_pallet IA-NS-2000814 Openlibrary_edition OL26837925M Openlibrary_work OL19547345W Page-progression lr Page_number_confidence 86.73 Pages 198 Partner Innodata Pdf_module_version 0.0.20 Ppi 360 Rcs_key 24143 Republisher_date 20221228010643 Republisher_operator associate-chaime-cadilig@archive.org;associate-kentvincent-yanong@archive.org Republisher_time 610 Scandate 20221217112115 Scanner station19.cebu.archive.org Scanningcenter cebu Scribe3_search_catalog isbn Scribe3_search_id 9781593275907 Tts_version 5.4-initial-3-gae281fbc Worldcat (source edition) 880566746
Black Hat Python, 2nd Edition


When it comes to creating powerful and effective hacking tools, Python is the language of choice for most security analysts. In this second edition of the bestselling Black Hat Python, you’ll explore the darker side of Python’s capabilities: everything from writing network sniffers, stealing email credentials, and bruteforcing directories to crafting mutation fuzzers, investigating virtual machines, and creating stealthy trojans.
All of the code in this edition has been updated to Python 3.x. You’ll also find new coverage of bit shifting, code hygiene, and offensive forensics with the Volatility Framework as well as expanded explanations of the Python libraries ctypes, struct, lxml, and BeautifulSoup, and offensive hacking strategies like splitting bytes, leveraging computer vision libraries, and scraping websites.
- Create a trojan command-and-control server using GitHub
- Detect sandboxing and automate common malware tasks like keylogging and screenshotting
- Extend the Burp Suite web-hacking tool
- Escalate Windows privileges with creative process control
- Use offensive memory forensics tricks to retrieve password hashes and find vulnerabilities on a virtual machine
- Abuse Windows COM automation
- Exfiltrate data from a network undetected
When it comes to offensive security, you need to be able to create powerful tools on the fly. Learn how with Black Hat Python.
Justin Seitz is the president and co-founder of Dark River Systems Inc., where he spends his time shipping Hunchly, consulting for hedge funds and doing OSINT research. He is the author of Gray Hat Python (No Starch Press), the first book to cover Python for security analysis.
Tim Arnold has worked as a professional Python software developer at the SAS Institute for more than 20 years. He contributes to several open source software projects and volunteers as a hacking trainer in his local community.
Foreword by Charlie Miller
Preface
Chapter 1: Setting up Your Python Environment
Chapter 2: Basic Networking Tools
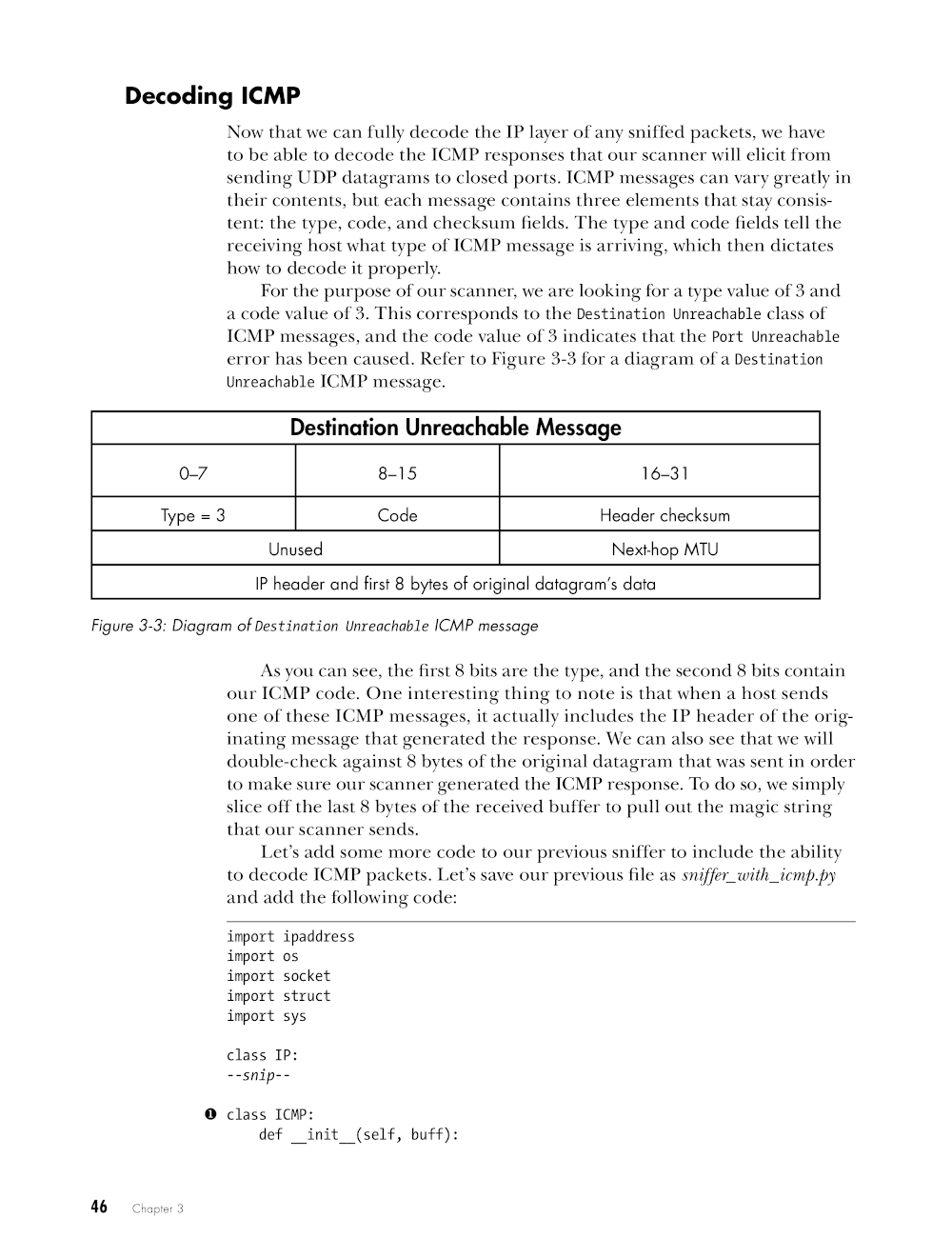
Chapter 3: Writing a Sniffer
Chapter 4: Owning the Network with Scapy
Chapter 5: Web Hackery
Chapter 6: Extending Burp Proxy
Chapter 7: GitHub Command and Control
Chapter 8: Common Trojaning Tasks on Windows
Chapter 9: Fun with Exfiltration
Chapter 10: Windows Privilege Escalation
Chapter 11: Offensive Forensics
Index
“Black Hat Python is a fun read written by experts with years of experience who are willing to share the secrets they have learned along the way. While It might not immediately turn you into a super stunt hacker like me, it will certainly get you started down the correct path.”
(from the foreword)
—Charlie Miller, Security Researcher
«If you work as a computer security professional and want to code in Python, this is definitely a book that belongs on your bookshelf.»
—Craig Mullins, Data and Technology Today
«An essential resource for anyone involved in offensive security or looking to improve their Python programming skills. Its comprehensive coverage, practical examples, and step-by-step instructions make it an invaluable tool for anyone looking to become a skilled hacker or penetration tester.»
—InfoSecNoobs.com
Reviews of the first edition of Black Hat Python:
Selected by Cyber Defense Magazine as 1 of 100 Best CyberSecurity Books
«Another incredible Python book. With a minor tweak or two many of these programs will have at least a ten year shelf life, and that is rare for a security book.»
—Stephen Northcutt, founding president of the SANS Technology Institute
«A great book using Python for offensive security purposes.»
—Andrew Case, Volatility core developer and coauthor of The Art of Memory Forensics
«If you truly have a hacker’s mindset, a spark is all you need to make it your own and do something even more amazing. Justin Seitz offers plenty of sparks.»
—Ethical Hacker
«Whether you’re interested in becoming a serious hacker/penetration tester or just want to know how they work, this book is one you need to read. Intense, technically sound, and eye-opening.»
—Sandra Henry-Stocker, IT World
«Definitely a recommended read for the technical security professional with some basic previous exposure to Python.»
—Richard Austin, IEEE Cipher
«This book breaks down how to create powerful tools using Python like network sniffers or keyloggers. This book even goes over how to escalate privileges in Windows.»
—Davin Jackson, Alpha Cyber Security, Books to Start Your Penetration Testing Journey
First Edition Resources
Black Hat Python
Read it now on the O’Reilly learning platform with a 10-day free trial.
O’Reilly members get unlimited access to books, live events, courses curated by job role, and more from O’Reilly and nearly 200 top publishers.
Book description
When it comes to creating powerful and effective hacking tools, Python is the language of choice for most security analysts. But just how does the magic happen?
In Black Hat Python, the latest from Justin Seitz (author of the best-selling Gray Hat Python), you’ll explore the darker side of Python’s capabilities—writing network sniffers, manipulating packets, infecting virtual machines, creating stealthy trojans, and more. You’ll learn how to:
- Create a trojan command-and-control using GitHub
- Detect sandboxing and automate common malware tasks, like keylogging and screenshotting
- Escalate Windows privileges with creative process control
- Use offensive memory forensics tricks to retrieve password hashes and inject shellcode into a virtual machine
- Extend the popular Burp Suite web-hacking tool
- Abuse Windows COM automation to perform a man-in-the-browser attack
- Exfiltrate data from a network most sneakily
When it comes to offensive security, your ability to create powerful tools on the fly is indispensable. Learn how in Black Hat Python.
Publisher resources
Table of contents
- Black Hat Python: Python Programming for Hackers and Pentesters
- Dedication
- About the Author
- About the Technical Reviewers
- Foreword
- Preface
- Acknowledgments
- 1. Setting Up Your Python Environment
- Installing Kali Linux
- WingIDE
- Python Networking in a Paragraph
- TCP Client
- UDP Client
- TCP Server
- Replacing Netcat
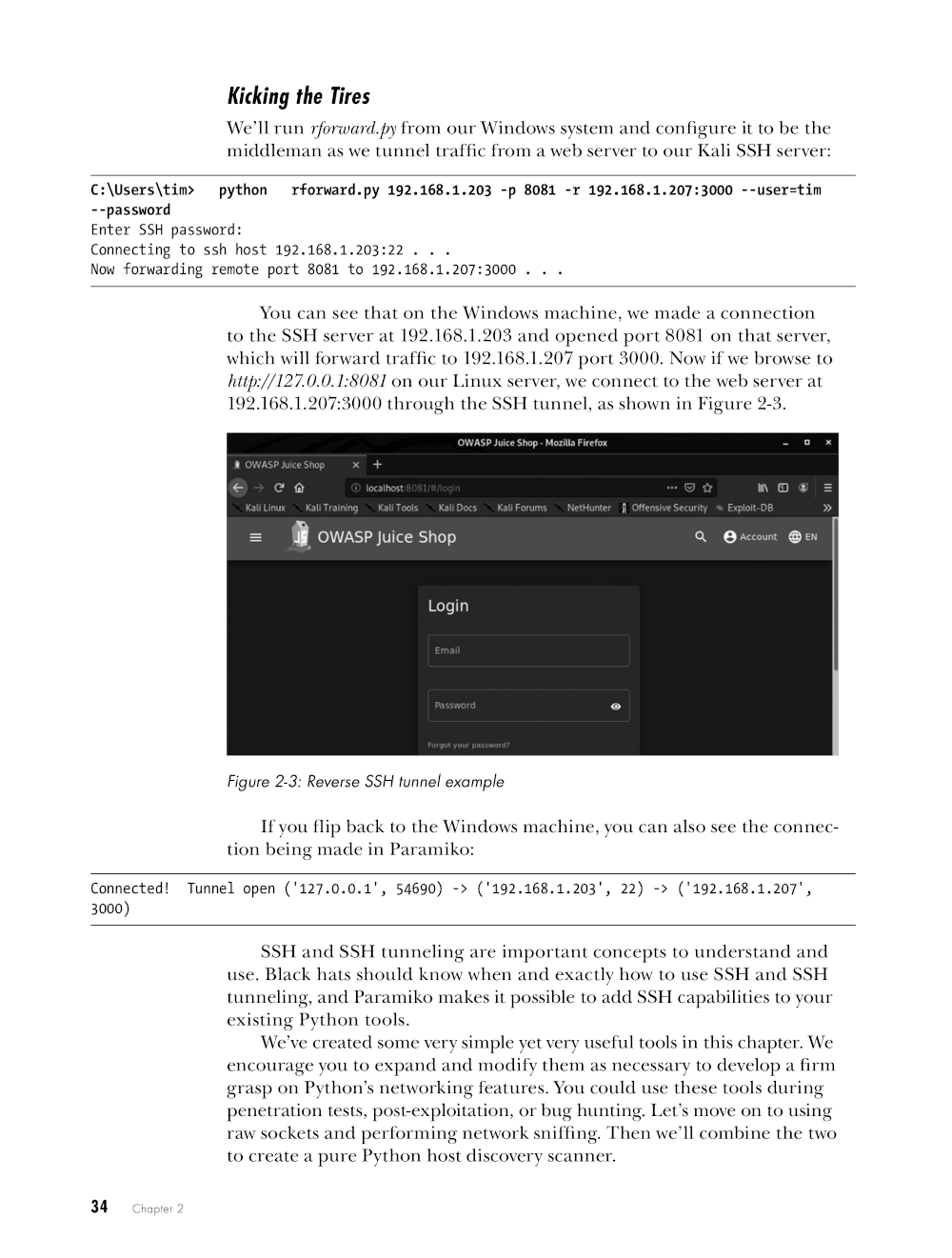
- Kicking the Tires
- Kicking the Tires
- Kicking the Tires
- Kicking the Tires
- Building a UDP Host Discovery Tool
- Packet Sniffing on Windows and Linux
- Kicking the Tires
- Kicking the Tires
- Kicking the Tires
- Stealing Email Credentials
- Kicking the Tires
- Kicking the Tires
- Kicking the Tires
- The Socket Library of the Web: urllib2
- Mapping Open Source Web App Installations
- Kicking the Tires
- Kicking the Tires
- Kicking the Tires
- Setting Up
- Burp Fuzzing
- Kicking the Tires
- Kicking the Tires
- Kicking the Tires
- Setting Up a GitHub Account
- Creating Modules
- Trojan Configuration
- Building a Github-Aware Trojan
- Hacking Python’s import Functionality
- Kicking the Tires
- Keylogging for Fun and Keystrokes
- Kicking the Tires
- Kicking the Tires
- Man-in-the-Browser (Kind Of)
- Creating the Server
- Kicking the Tires
- Kicking the Tires
- Installing the Prerequisites
- Creating a Process Monitor
- Process Monitoring with WMI
- Kicking the Tires
- Kicking the Tires
- Kicking the Tires
- Installation
- Profiles
- Grabbing Password Hashes
- Direct Code Injection
- Kicking the Tires
Product information
- Title: Black Hat Python
- Author(s): Justin Seitz
- Release date: December 2014
- Publisher(s): No Starch Press
- ISBN: 9781593275907
You might also like
Check it out now on O’Reilly
Dive in for free with a 10-day trial of the O’Reilly learning platform—then explore all the other resources our members count on to build skills and solve problems every day.
![[WorldCat (this item)]](https://archive.org/images/worldcat-small.png)